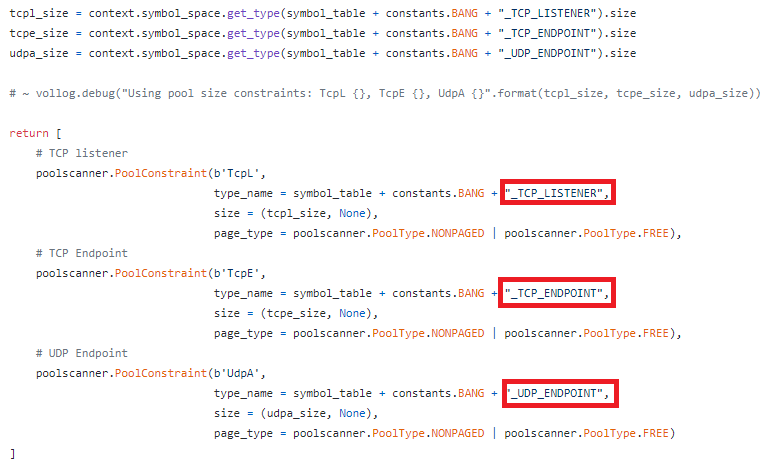
I’ve been reading “The art of memory forensics”, on chapter 11 page 327 they added the output of Windbg dt(_TCP_ENDPOINT)
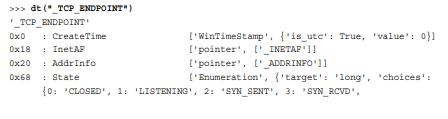
I have been trying to get the same result with Windbg but I keep getting the same error -
dt(_TCP_ENDPOINT) Symbol _TCP_ENDPOINT not found.
even though I loaded the tcpip.sys symbols file
1: kd> lml start end module name … fffff8053bfc0000 fffff8053c2a9000 tcpip (pdb symbols) C:\ProgramData\Dbg\sym\tcpip.pdb\4EF7BCB071F28E1DAAAA937D59B39D121\tcpip.pdb
I dont get this kind of error when looking other Kernel structures,
1: kd> dt(_EPROCESS) ntdll!_EPROCESS +0x000 Pcb : _KPROCESS +0x2e0 ProcessLock : _EX_PUSH_LOCK …
What am I doing wrong?
That book was written in 2005, right? Things have changed, systems get redesigned. Perhaps that structure is no longer used.
Hey, The book was written in 2014 and they were referring to a structure that exists in windows 7.
so initially I thought that was the case, but when I looked into the plugin source code, I saw that they were using the same names.
This plugin ran perfectly on a similar crash dump of Windows 10.
Github source code - https://github.com/volatilityfoundation/volatility3/blob/master/volatility/framework/plugins/windows/netscan.py
Thanks,
It was a stupid mistake,
The output in the book was from the dt() command from the volshell plugin in volatility 2.7, not Windbg.
_TCP_ENDPOINT is an overlay used by Volatility -
http://axlotldunktank.blogspot.com/p/volshell.html