Hello,
I have some detailed question about the following quote:
@“Wilhelm_Nöker” said:
@Tim_Roberts said:
Starting July 2021, can we still sign and install a driver signed with a trusted cross-certificate on a Windows 10 machine…?
No. They are shutting down the whole cross-signing ecosystem. The cross certificates will all expire and no more will be created.
Exactly. And because that’s how the policy change works (i.e. they don’t have to roll out any specific Windows updates, they will just sit and let things happen), July 2021 is not even the date to worry about. Depending on your certificate provider, your ability to create valid cross-signed drivers will end much sooner: in April or February 2021.
I understand, that if they do not allow ACs to sell any more cross certificates, the existing cross certificates will start disapeare and thus at one point in time no more cross signign will be possible. Effectivly cross signign dies out.
But assume, you still have a code signing Certificate from any AC with cross signign capablity and both, the certificate itself and the cross certificate are valid beyond 30. June 2021.
Is it then possible and ok (with MS compliance) to sign your driver with that certificate? Will that work?
I would propse a yes: Cause I cannot image how Microsoft will pe able to force the policy on the clients with the deadline 30. June 2021? That would either require a Windows Update on clients, which in fact is not possible any more on Win 7, right? Or the have some easter egg programmed into Win 7, which revokes drivers with certificates that are valid longer than 30. June 2021? Later sounds a bit strange to me.
And to dig even more into the nasty documentaiton of Microsoft Policies.
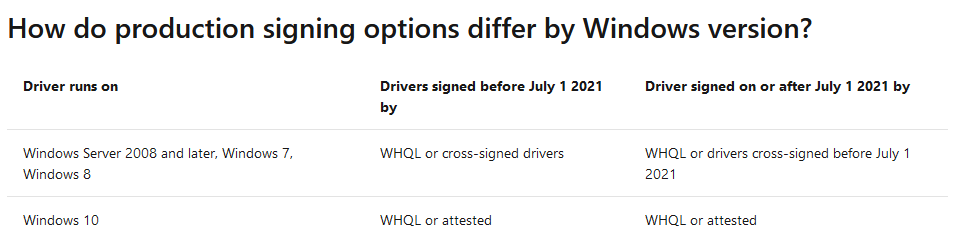
On this page: Deprecation of Software Publisher Certificates, Commercial Release and Test Certificates - Windows drivers | Microsoft Learn) Mircosoft does not mention any specific date in the whole text except for that strange Table on the bottom of the page.
Moreover they state at the beginning of the page:
Existing cross-signed root certificates with kernel mode code signing capabilities will continue working until expiration
A little bit more down the page they say: The majority of cross-signed root certificates will expire in 2021
But on the same page, the have a hyperlink to this page: Cross-Certificates for Kernel Mode Code Signing - Windows drivers | Microsoft Learn. And there you’ll find a list containing cross certificates which a valid till 2023 or even 2025 (e.g. Entrust Root Certification Authority – G2 d8 fc 24 87 48 58 5e 17 3e fb fb 30 75 c4 b4 d6 0f 9d 8d 08).
So taking all this together, what’s the real meaning and final impact of this table on the first page?:
I’m again asking the question from the beginning of my post:
How do the come to say there is a deadline on 30. June 2021? How would the enforce this policy?
Hoping anybody here can give me a satisfying answer 
Greetings Matthias