Hi,
I am working on minifilter driver which tracks whether file is modified or not.
In order to to so have minifilter write-callback registered i.e {IRP_MJ_WRITE, 0, PreWrite, NULL},
In Test environment sample.exe is run using cmd.exe or command prompt (Windows 7 32 bit).
There are some writes which are done by cmd.exe on executable and I think those are missed by minifilter as per my observation.
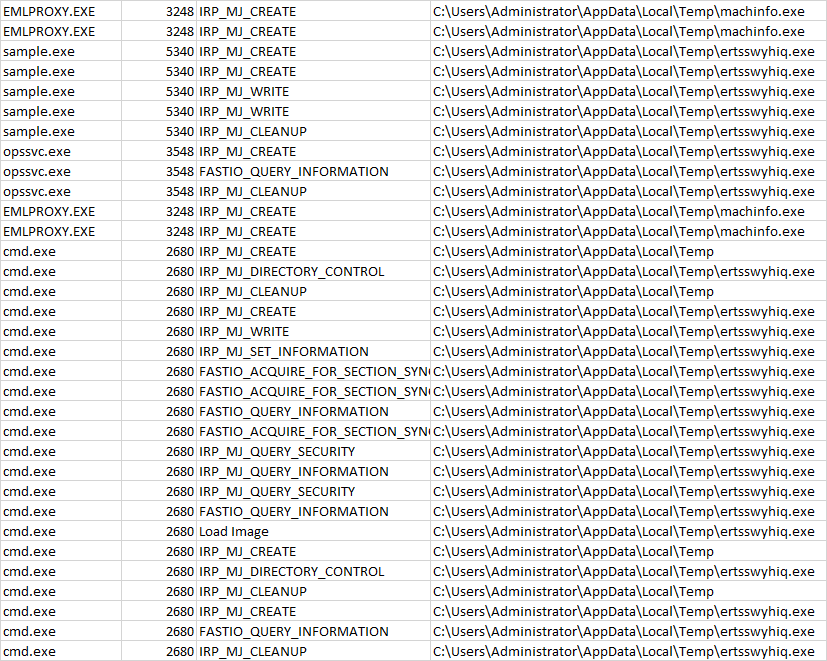
in order to get the stack ran procmon and collected logs.
EMLPROXY.EXE 3248 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\machinfo.exe
EMLPROXY.EXE 3248 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\machinfo.exe
sample.exe 5340 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
sample.exe 5340 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
sample.exe 5340 IRP_MJ_WRITE C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
sample.exe 5340 IRP_MJ_WRITE C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
sample.exe 5340 IRP_MJ_CLEANUP C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
opssvc.exe 3548 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
opssvc.exe 3548 FASTIO_QUERY_INFORMATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
opssvc.exe 3548 IRP_MJ_CLEANUP C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
EMLPROXY.EXE 3248 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\machinfo.exe
EMLPROXY.EXE 3248 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\machinfo.exe
cmd.exe 2680 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp
cmd.exe 2680 IRP_MJ_DIRECTORY_CONTROL C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 IRP_MJ_CLEANUP C:\Users\Administrator\AppData\Local\Temp
cmd.exe 2680 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 IRP_MJ_WRITE C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe ::: I think this is missed by minifilter
cmd.exe 2680 IRP_MJ_SET_INFORMATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 FASTIO_ACQUIRE_FOR_SECTION_SYNCHRONIZATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 FASTIO_ACQUIRE_FOR_SECTION_SYNCHRONIZATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 FASTIO_QUERY_INFORMATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 FASTIO_ACQUIRE_FOR_SECTION_SYNCHRONIZATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 IRP_MJ_QUERY_SECURITY C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 IRP_MJ_QUERY_INFORMATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 IRP_MJ_QUERY_SECURITY C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 FASTIO_QUERY_INFORMATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 Load Image C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp
cmd.exe 2680 IRP_MJ_DIRECTORY_CONTROL C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 IRP_MJ_CLEANUP C:\Users\Administrator\AppData\Local\Temp
cmd.exe 2680 IRP_MJ_CREATE C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 FASTIO_QUERY_INFORMATION C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
cmd.exe 2680 IRP_MJ_CLEANUP C:\Users\Administrator\AppData\Local\Temp\ertsswyhiq.exe
Call stack of writefile of cmd.exe.
0 fltmgr.sys FltRequestOperationStatusCallback + 0xeb5 0x8db9daeb C:\Windows\system32\drivers\fltmgr.sys
1 fltmgr.sys FltGetIrpName + 0xc5c 0x8dba09f0 C:\Windows\system32\drivers\fltmgr.sys
2 fltmgr.sys FltGetIrpName + 0x116d 0x8dba0f01 C:\Windows\system32\drivers\fltmgr.sys
3 fltmgr.sys FltGetIrpName + 0x1626 0x8dba13ba C:\Windows\system32\drivers\fltmgr.sys
4 ntoskrnl.exe IofCallDriver + 0x64 0x83c74f44 C:\Windows\system32\ntoskrnl.exe
**5 ntoskrnl.exe IoSynchronousPageWrite + 0x19d 0x83cdfe9e C:\Windows\system32\ntoskrnl.exe
**6 ntoskrnl.exe RtlSidHashInitialize + 0x8b5 0x83cacf8e C:\Windows\system32\ntoskrnl.exe
7 ntoskrnl.exe KeReleaseGuardedMutex + 0x157a 0x83ce1aa4 C:\Windows\system32\ntoskrnl.exe
8 ntoskrnl.exe CcFlushCache + 0x329 0x83cad7f5 C:\Windows\system32\ntoskrnl.exe
9 ntoskrnl.exe ExfTryToWakePushLock + 0x4f7 0x83cd23a7 C:\Windows\system32\ntoskrnl.exe
10 ntoskrnl.exe FsRtlInsertPerFileObjectContext + 0x293 0x83cf7610 C:\Windows\system32\ntoskrnl.exe
11 ntoskrnl.exe MmCreateSection + 0x333 0x83e7ad54 C:\Windows\system32\ntoskrnl.exe
12 ntoskrnl.exe NtCreateSection + 0x16e 0x83e98fe3 C:\Windows\system32\ntoskrnl.exe
13 ntoskrnl.exe ZwYieldExecution + 0xb5a 0x83c7b79a C:\Windows\system32\ntoskrnl.exe
14 ntoskrnl.exe ZwCreateSection + 0x11 0x83c793a1 C:\Windows\system32\ntoskrnl.exe
15 ntoskrnl.exe ZwYieldExecution + 0xb5a 0x83c7b79a C:\Windows\system32\ntoskrnl.exe
16 ntdll.dll ZwCreateUserProcess + 0xc 0x77b64bcc C:\Windows\System32\ntdll.dll
17 kernel32.dll CreateProcessInternalW + 0x75d 0x76224a0b C:\Windows\System32\kernel32.dll
18 kernel32.dll CreateProcessW + 0x2c 0x761d2059 C:\Windows\System32\kernel32.dll
19 cmd.exe cmd.exe + 0x9774 0x4a339774 C:\Windows\System32\cmd.exe
20 cmd.exe cmd.exe + 0x93b4 0x4a3393b4 C:\Windows\System32\cmd.exe
21 cmd.exe cmd.exe + 0x4927 0x4a334927 C:\Windows\System32\cmd.exe
22 cmd.exe cmd.exe + 0x23c0 0x4a3323c0 C:\Windows\System32\cmd.exe
23 cmd.exe cmd.exe + 0x50b8 0x4a3350b8 C:\Windows\System32\cmd.exe
24 cmd.exe cmd.exe + 0x61a0 0x4a3361a0 C:\Windows\System32\cmd.exe
25 kernel32.dll BaseThreadInitThunk + 0x12 0x76221174 C:\Windows\System32\kernel32.dll
26 ntdll.dll RtlInitializeExceptionChain + 0x63 0x77b7b3f5 C:\Windows\System32\ntdll.dll
27 ntdll.dll RtlInitializeExceptionChain + 0x36 0x77b7b3c8 C:\Windows\System32\ntdll.dll
I tried to register callback for IRP_MJ_MDL_WRITE_COMPLETE,IRP_MJ_PREPARE_MDL_WRITE as well but no luck. write is not tracked.
Any inputs would be appreciated ??