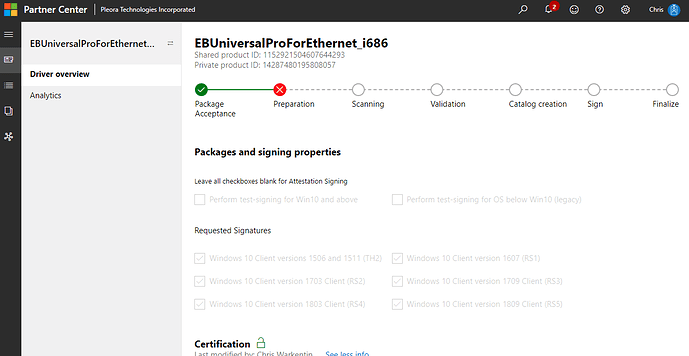
I’m trying to sign our driver using the same procedure I always have and it’s failing but not giving me any feedback as to why.
Our build server builds the driver, signs it with our EV cert, puts it all in a .cab file and then signs that with the EV cert. We haven’t needed to re-sign the driver since October so maybe something has changed? It stops at ‘Preparation’ and then sends me a bajillion emails with a link for more information that contains no more information.
Help? This is a software driver with NDIS and WDM interfaces.
Same here.
Only we did successfully sign severl drivers yesterday, then one
failed, got several e-mails (not one as expected!).
The page shows no extra information, just a red crossout under Preparation.
On 2/14/19, Chris_Warkentin wrote:
> OSR https://community.osr.com/
> Chris_Warkentin started a new discussion: Attestation signing failing with
> no feedback
>
> I’m trying to sign our driver using the same procedure I always have and
> it’s failing but not giving me any feedback as to why.
>
> Our build server builds the driver, signs it with our EV cert, puts it all
> in a .cab file and then signs that with the EV cert. We haven’t needed to
> re-sign the driver since October so maybe something has changed? It stops at
> ‘Preparation’ and then sends me a bajillion emails with a link for more
> information that contains no more information.
>
> Help? This is a software driver with NDIS and WDM interfaces.
>
> –
> Reply to this email directly or follow the link below to check it out:
> https://community.osr.com/discussion/291062/attestation-signing-failing-with-no-feedback
>
> Check it out:
> https://community.osr.com/discussion/291062/attestation-signing-failing-with-no-feedback
>
Maybe a problem on their end? Is anyone else able to sign right now? It’s frustrating to get no feedback at all.
AHA! I figured it out. For some reason there is another certificate on the build server now that matches criteria but has a later expiry date and it was getting picked instead.
I changed the signtool argument to explicitly use the SHA1 and voila! We’re in business.
How’d you get all those different Win10 client versions to show up in the “Requested Signatures” section?
They are there by default.
In my case, it is not the cert, we have only one valid cert.
I did not retry the process yet.
@Shane_Corbin said:
How’d you get all those different Win10 client versions to show up in the “Requested Signatures” section?
I always get the lot of them - i686, x64 and ARM. I have to pick the subset to match the version I’m signing.
I picked all, including ARM, and the signing did not fail before.